FreeRASP for iOS is a lightweight and easy-to-use mobile app protection and security monitoring SDK. It is designed to combat reverse engineering, tampering, or similar attack attempts. FreeRASP covers several attack vectors and enables you to set a response to each threat.
iOS version detects security issues such as:
- App installed on a jailbroken device (e.g., unc0ver, check1rain, ...)
- Runtime manipulations (e.g., Shadow or Frida) or running the app in the simulator
- Tampering with the application
- Attaching a debugger to the application
To learn more about freeRASP features, visit our main GitHub repository.
The installation guide will lead you through the whole implementation, such as adding the SDK to the dependencies, configuring it for your app, handling detected threats. It will also instruct you about required user data policies.
- Copy folder
Talsecinto your Application folder - Drag & drop Talsec folder to your
.xcworkspace - Add TalsecRuntime framework to Target > Build Phases > Link Binary With Libraries
- In the General > Frameworks, Libraries, and Embedded Content choose Embed & Sign
Note: In case you are using Carthage, the zipped version of frameworks are included in the Releases.
- In the
AppDelegateimportTalsecRuntimeand add the following code (e.g., in thedidFinishLaunchingWithOptionsmethod.:
let config = TalsecConfig(appBundleIds: ["YOUR_APP_BUNDLE_ID"], appTeamId: "YOUR TEAM ID", watcherMailAddress: "WATCHER EMAIL ADDRESS", isProd: true)
Talsec.start(config: config)The value of watcherMail is automatically used as the target address for your security reports. Mail has a strict form '[email protected]'.
The Debug version is used to not complicate the development process of the application, e.g. if you would implement killing of the application on the debugger callback. It disables some checks which won't be triggered during the development process:
- Debugging
- Tampering
- Simulator
- Unofficial store
If you want to use the Debug version, set the isProd parameter to false. Make sure, that you have the Release version in the production (i.e. isProd set to true)!
Anywhere in your project, add the following code as an extension:
import TalsecRuntime
extension SecurityThreatCenter: SecurityThreatHandler {
public func threatDetected(_ securityThreat: TalsecRuntime.SecurityThreat) {
print("Found incident: \(securityThreat.rawValue)")
}
}If you decide to kill the application from the callback, make sure that you use an appropriate way of killing it. Use the code above for handling these types of threats:
public enum SecurityThreat: String, Codable, CaseIterable, Equatable {
/// app integrity / repackaging / tampering
case signature = "appIntegrity"
/// jailbreak
case jailbreak = "privilegedAccess"
/// debugger
case debugger = "debug"
/// runtime manipulation / hooks
case runtimeManipulation = "hooks"
/// disabled passcode
case passcode
/// passcode change
case passcodeChange
/// simulator
case simulator
/// missing Secure Enclave
case missingSecureEnclave
/// device binding
case deviceChange = "device binding"
/// changed deviceID
case deviceID
/// unofficial store or Xcode build
case unofficialStore
}To learn more about these checks, visit our wiki page that provides an explanation for them.
See the generic info about freeRASP data collection here.
App Store App Privacy Details indicate that applications should inform users of the data that they are collecting and processing, and therefore Apple rejects the apps which do not comply with the policy. To comply with the policy, in the App Privacy section, it is important to check the following:
- Identifiers -> Device ID -> App Functionality
- It is an anonymous device identifier for the App vendor as per: https://developer.apple.com/documentation/uikit/uidevice/1620059-identifierforvendor
- Talsec Security SDK can not link the device identifier to the user
- Diagnostics -> Performance Data -> App Functionality, Other Purposes, No for linking to the user
- Diagnostics -> Other diagnostics data -> App Functionality, Other Purposes, No for linking to the user
- Other data -> App Functionality, No for linking to the user
- Security diagnostics data (such as jailbreak)
It is also essential to include the information in the privacy policy of the application, see the Data Collection, Processing, and GDPR compliance.
After installation, please go through this checklist to avoid potential issues or solve them quickly.
And you're done 🎉! You can open an issue if you get stuck anywhere in the guide or show your appreciation by starring this repository ⭐!
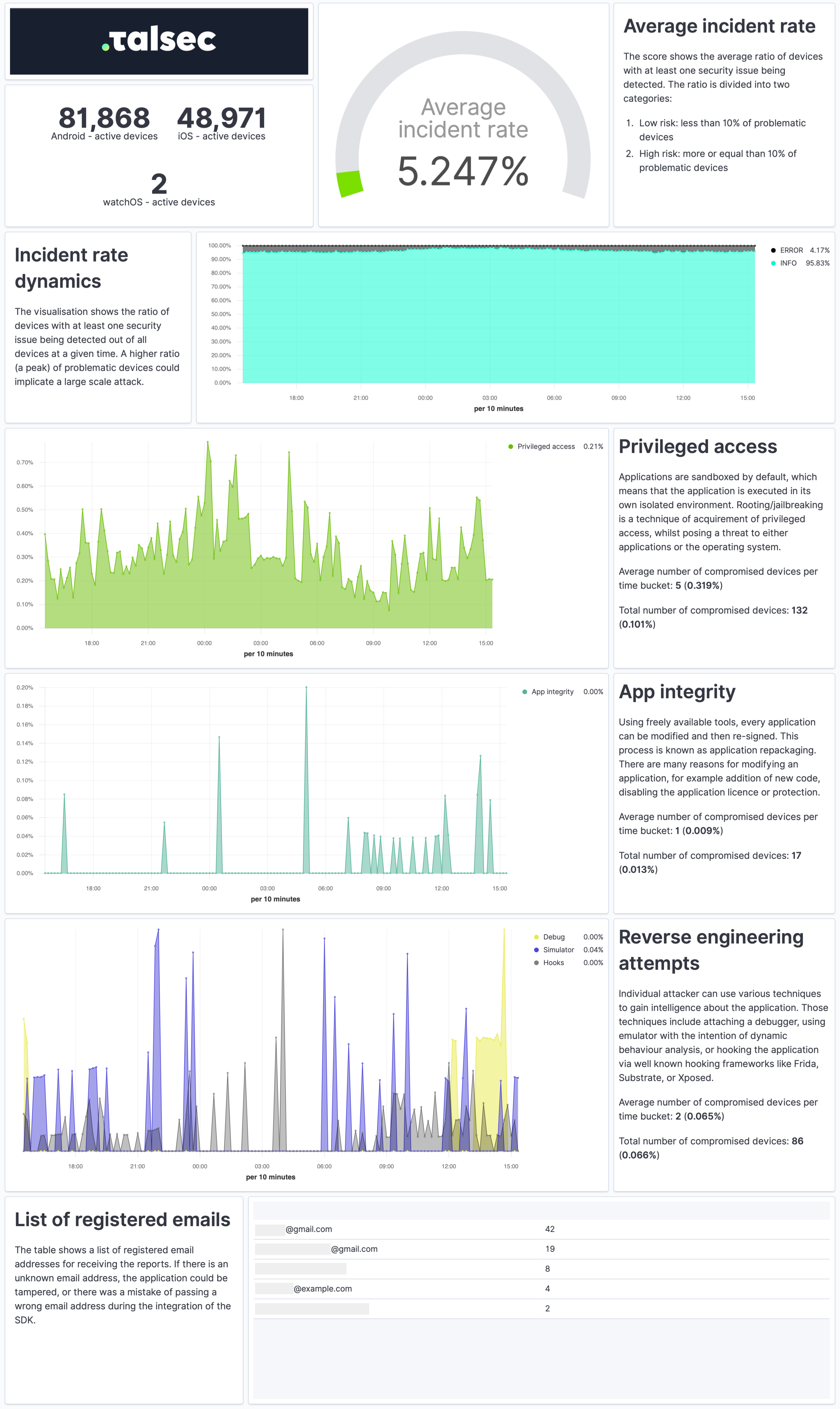
The Security Report is a weekly summary describing the application's security state and characteristics of the devices it runs on in a practical and easy-to-understand way.
The report provides a quick overview of the security incidents, their dynamics, app integrity, and reverse engineering attempts. It contains info about the security of devices, such as OS version or the ratio of devices with screen locks and biometrics. Each visualization also comes with a concise explanation.
To receive Security Reports, fill out the watcherMail field in Talsec config.
Talsec offers commercial plans on top of freeRASP (Business RASP+):
- No limits of Fair Usage Policy (100K App Downloads)
- No Data Collection from your app
- FinTech grade security, features and SLA (see more in this post)
- Protect APIs and risk scoring by AppiCrypt®
Learn more at talsec.app.
Not to overlook, the one of the most valued commercial features is AppiCrypt® - App Integrity Cryptogram.
It allows easy-to-implement API protection and App Integrity verification on the backend to prevent API abuse:
- Bruteforce attacks
- Botnets
- API abuse by App impersonation
- Session-hijacking
- DDoS
It is a unified solution that works across all mobile platforms without dependency on external web services (i.e., without extra latency, an additional point of failure, and maintenance costs).
Learn more about commercial features at talsec.app.
TIP: You can try freeRASP and then upgrade easily to an enterprise service.
freeRASP is freemium software i.e. there is a Fair Usage Policy (FUP) that impose some limitations on the free usage. See the FUP section in the table below| freeRASP | Business RASP+ | |||
|---|---|---|---|---|
| Runtime App Self Protection (RASP, app shielding) | ||||
| Advanced root/jailbreak protections (including Magisk) | basic | advanced | ||
Runtime reverse engineering controls
|
basic | advanced | ||
Runtime integrity controls
|
basic | advanced | ||
Device OS security status check
|
yes | yes | ||
UI protection
|
no | yes | ||
| Hardening suite | ||||
Security hardening suite
|
no | yes | ||
| AppiCrypt® - App Integrity Cryptogram | ||||
| API protection by mobile client integrity check, online risk scoring, online fraud prevention, client App integrity check. The cryptographic proof of app & device integrity. | no | yes | ||
| Security events data collection, Auditing and Monitoring tools | ||||
| Threat events data collection from SDK | yes | configurable | ||
| AppSec regular email reporting service | yes (up to 100k devices) | yes | ||
| UI portal for Logging, Data analytics and auditing | no | yes | ||
| Support and Maintenance | ||||
| SLA | Not committed | yes | ||
| Maintenance updates | Not committed | yes | ||
| Fair usage policy | ||||
| Mentioning of the App name and logo in the marketing communications of Talsec (e.g. "Trusted by" section on the web). | over 100k downloads | no | ||
| Threat signals data collection to Talsec database for processing and product improvement | yes | no | ||
For further comparison details (and planned features), follow our discussion.
Talsec is an academic-based and community-driven mobile security company. We deliver in-App Protection and a User Safety suite for Fintechs. We aim to bridge the gaps between the user's perception of app safety and the strong security requirements of the financial industry.
Talsec offers a wide range of security solutions, such as App and API protection SDK, Penetration testing, monitoring services, and the User Safety suite. You can check out offered products at our web.
This project is provided as freemium software i.e. there is a fair usage policy that impose some limitations on the free usage. The SDK software consists of opensource and binary part which is property of Talsec. The opensource part is licensed under the MIT License - see the LICENSE file for details.