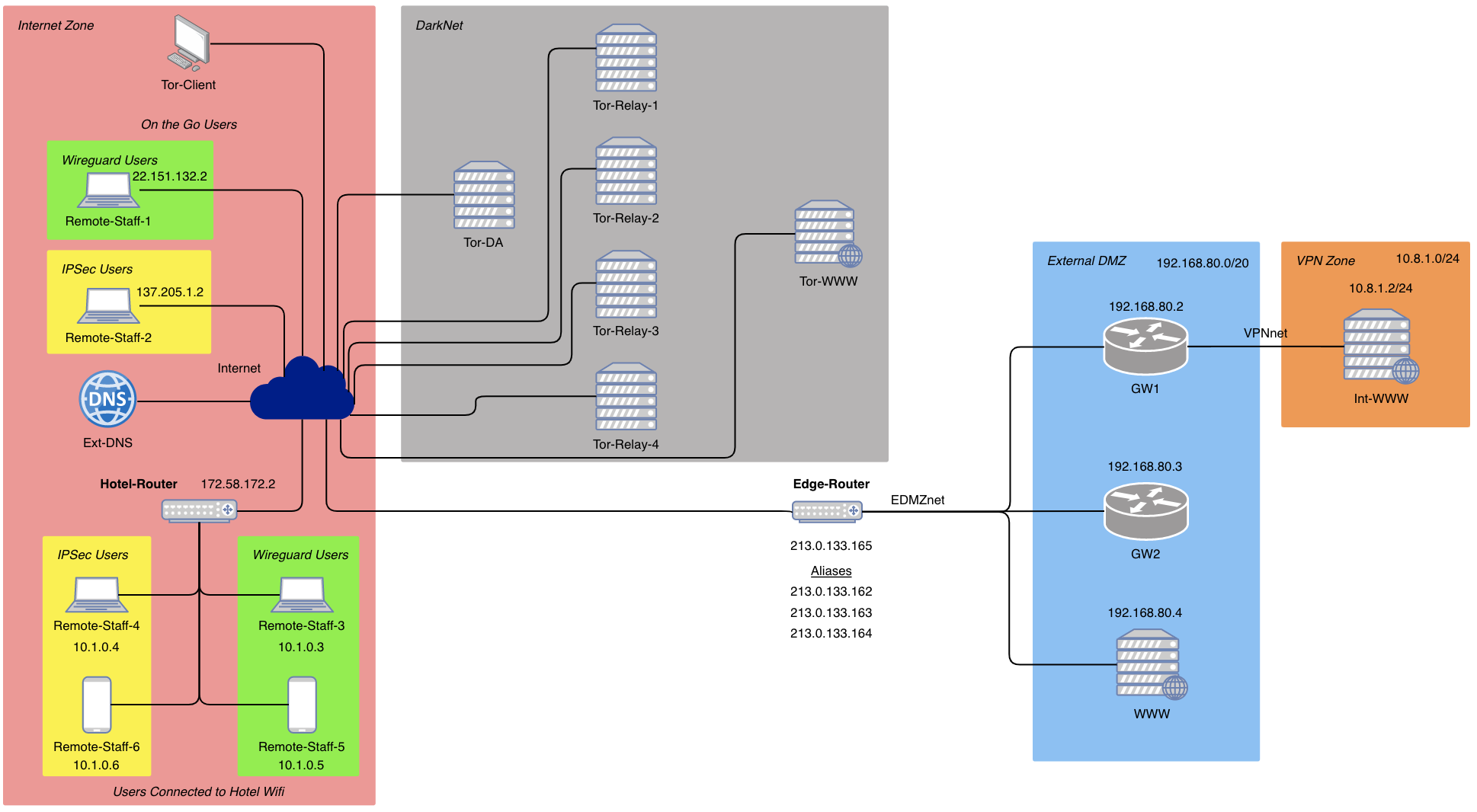
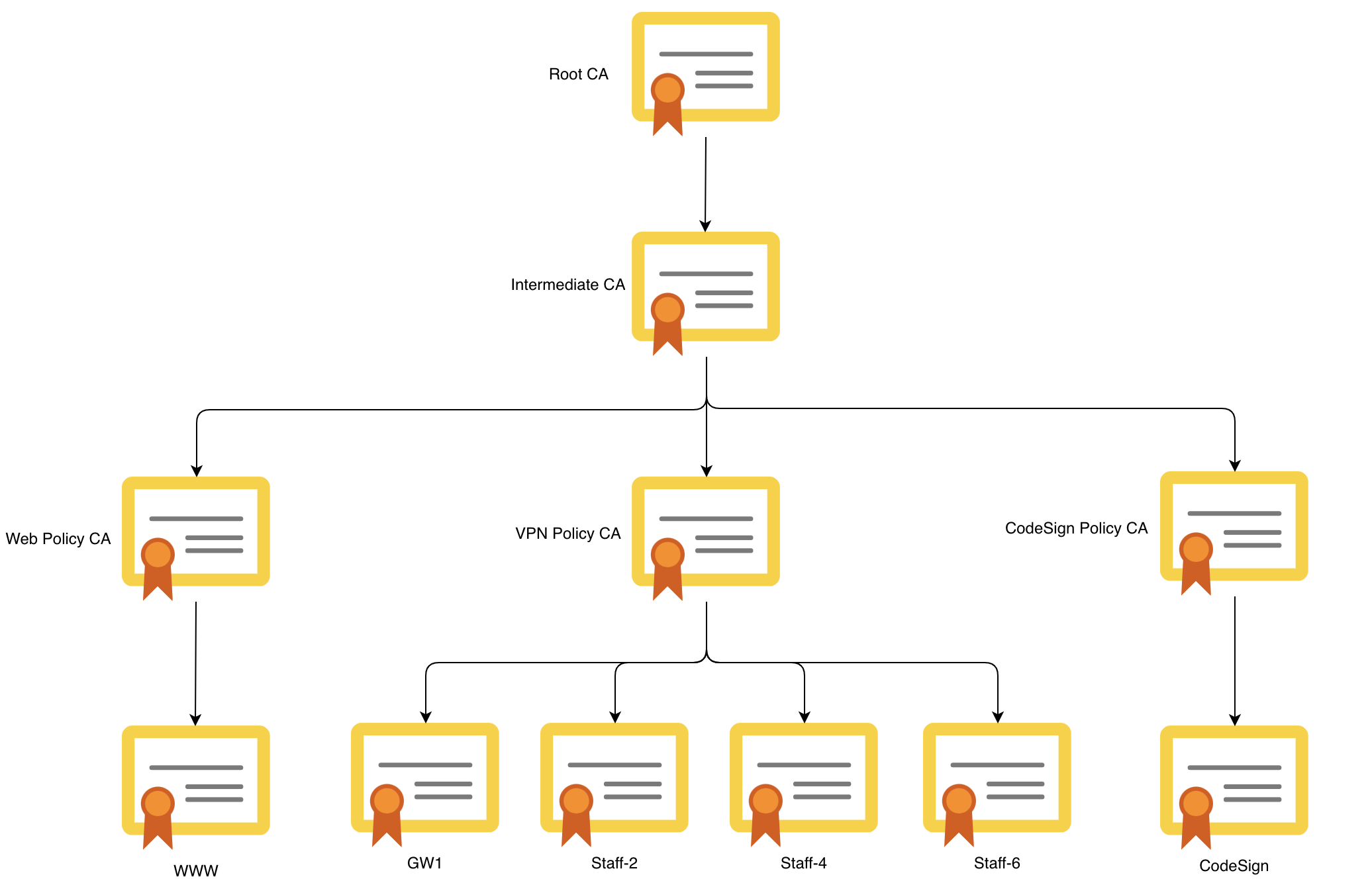
A scalable PKI infrastructure with a three tier certificate authority hierarchy with automated certificates generation and deployment. It housed StrongSwan IPSec gateway and a WireGuard VPN gateway. MACSec was configured for LAN-LAN Data Link Layer encryption with replay protection. A DarkNet is set up using an isolated TOR environment with a private TOR directory authority and relays.
- 1. satisfy the case-sensitive file-naming requirements of the deliverable files.
- 2. define and implement a credible x509 certificate hierarchy, consistent with the script of instructions.
- 3. submit a GPG public key that is consistent and valid until at least November 2023.
- 4. provide the correct GPG fingerprint of the public key on the front cover of your pdf submission.
- 5. have a digital signature that successfully verifies the submitted targz against the supplied public key.
- 6. achieve VPN connectivity for at least one sample mobile worker over IPSec.
- 7. have evidence that the VPN functions correctly.
- 8. correctly use allocated IP addresses and domain names.
- 9. have hashes at the demonstration that match the hashes in the submission.
- 10. make a compelling case for your scalable design and implementation of the IPSec VPN using the x509 certificate authority hierarchy as appropriate, permitting multiple workers to achieve connectivity.
- 11. have your submitted public key signed by at least three other submitted public keys.
- 12. have correctly used the private key associated with the submitted public key, to sign three other submitted public keys.
- 13. have clean, robust, maintainable, well organised, well commented configuration files throughout.
- 14. respond successfully to the challenge, encrypted against the public key that you submitted as a deliverable.
- 15. implement several sample mobile workers with successful VPN connectivity to both gateways.
- 16. make a succinct but compelling evaluation of your VPN configurations.
- 17. implement a robust HTTPS configuration of the Apache web-server.
- 18. make a compelling case for your HTTPS implementation.
- 19. make thoughtful use of sub-keys, key size and key validity periods in your submission.
- 20. have your signed public key, available on as many of the following keyservers as are functional just prior to the submission deadline:
- 21. demonstrate comprehensive mastery of all aspects of the the submission at all scales (detail through to overall concept). This should be reinforced by at least one additional crypto related feature of your choice.
- Implementation of 3 tier x509 certificate hierarchy.
- Layer 2 encryption using MACSec.
- Implementation of DarkNet using TOR.
- DarkWeb using TOR Hidden Services.
- Automation of x509 certificates generation.
- Automation of certificates deployment.
- Apache2 configuration against CRIME attacks.
cd cdp-pma-starterchmod +x /shared/deploy_certificates.sh start_lab.sh- To start entire lab without Tor infrastructure
./start_lab.sh- To start entire lab with Tor infrastructure
./start_lab.sh --with-tor- To start Tor infrastructure
./start_lab.sh --tor-only- To start IPSec infrastructure
./start_lab.sh --ipsec- To start WireGuard infrastructure
./start_lab.sh --wg