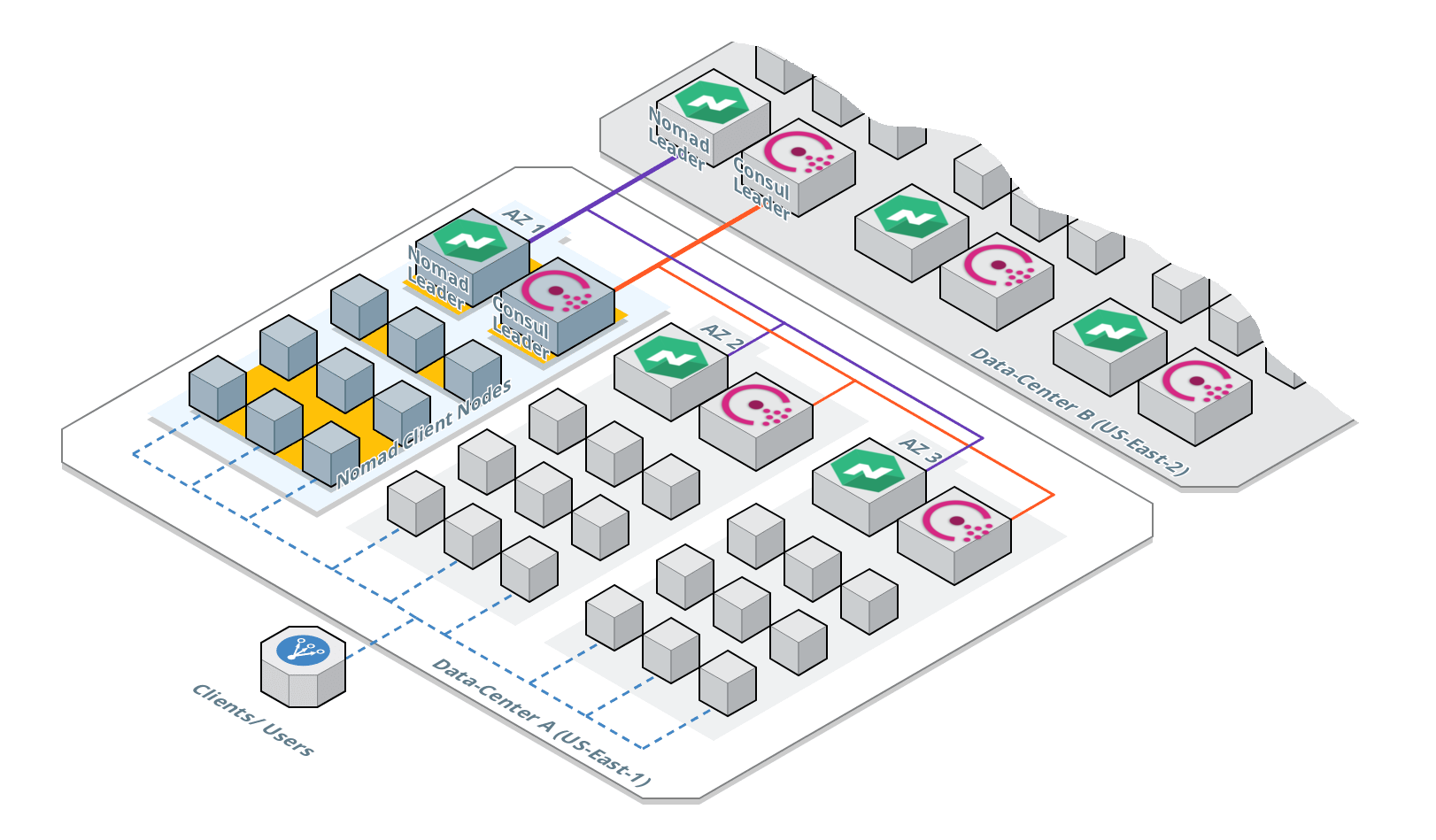
Please note that the original design goal of this role was more concerned with the initial installation and bootstrapping environment, which currently does not involve performing continuous maintenance, and therefore are only suitable for testing and development purposes, should not be used in production environments. The author does not guarantee the accuracy, completeness, reliability, and availability of the role content. Under no circumstances will the author be held responsible or liable in any way for any claims, damages, losses, expenses, costs or liabilities whatsoever, including, without limitation, any direct or indirect damages for loss of profits, business interruption or loss of information.
请注意,此角色的最初设计目标更关注初始安装和引导环境,目前不涉及执行连续维护,因此仅适用于测试和开发目的,不应在生产环境中使用。作者不对角色内容之准确性、完整性、可靠性、可用性做保证。在任何情况下,作者均不对任何索赔,损害,损失,费用,成本或负债承担任何责任,包括但不限于因利润损失,业务中断或信息丢失而造成的任何直接或间接损害。
Table of Contents
- Overview
- Architecture
- Instructions
- Requirements
- Role variables
- Dependencies
- Example Playbook
- License
- Author Information
- Donations
Consul is software for DNS-based service discovery and provides distributed Key/Value storage, segmentation and configuration. Registered services and nodes can be queried using a DNS interface or an HTTP interface. Consul is a service networking solution to connect and secure services across any runtime platform and public or private cloud. Consul is actually 4 services combined seamlessly into a single service. that have been combined into one. These individual services are:
All boxes (Kubernetes Control Plane, MySQL servers, Nginx servers, Syslog servers, NTP server, API servers…etc) will have the Consul agent daemon running on them which will notify the Consul server of its existence and the type of service it offers. The Consul server will register that box under the given service name, of which multiple other boxes can be members of. Then when DNS lookup request comes in for a given service then the Consul service will provide the IP address of one of the boxes in the service cluster, in a round-robin fashion.
The Consul agent will also give information about what health checking should be done on the box to see if it is a function.
Applications can make use of Consul's hierarchical Key/Value store for any number of purposes, including dynamic configuration, feature flagging, coordination, leader election, and more. The simple HTTP API makes it easy to use.
Consul supports multiple datacenters out of the box. This means users of Consul do not have to worry about building additional layers of abstraction to grow to multiple regions. In Consul 'Datacenter' is a logical concept that lets you can separate out your boxes into the data center. Which Datacenter a particular box belongs to is defined in that Consul agent's Consul file.
What advantages offers:
- It can replace get rid of Internal load balancers. The round-robin DNS system and the health checking features make Consul a good alternative to Load Balancers.
- The Key/Value store is a nice tool (with a GUI frontend) that can be used for config management when Alongside Consul Templates. This is a potential alternative to tools like Puppet’s hiera.
- You can define multiple datacenters (similar to environments) and each datacenter has it’s own Key/Value datastore. This is a powerful way to store your dev Key/Value separately from your prod Key/Value store.
- It does health-checking of nodes in a cluster and doesn’t send traffic to nodes while they are faulty. The fact that the Health Checking Service is deeply linked to the Service, it means that the resulting DNS service that Consul provides dynamic+intelligently updates to ensure traffic only gets sent to healthy hosts.
- Health checking is done locally by the Consul agents. This means that health checking is distributed and no need to have a pool of monitoring servers (e.g. Prometheus servers) to do the health checks. This means that health checking can easily be scaled to thousands of servers without any performance issues. Traditionally health-checking is also done by Load Balancers, but that’s no longer required either with this distributed health checking setup.
- Due to the distributed health checking setup. It means that health checks can be performed at a more frequent rate, e.g. once every second! This is something that’s not possible with more traditional monitoring software, because of performance issues.
- Any health-check failures are reported using the peer-to-peer gossip protocol amongst its own cluster. This means that it reduces traffic between the Consul server and clients.
- Changes in Key/Value can result in changes in near real-time.
- The Key/Value store is highly available – each Consul keeps an up to date local copy of the entire Key/Value store.
- You can register external services to Consul server, e.g. the official AWS NTP service.
- Consul and Docker works really well together.
This Ansible role installs HashiCorp Consul on Linux or Windows operating system, including establishing a filesystem structure and server configuration with some common operational features, Will works on the following operating systems:
- CentOS 7
- Rocky 8
- Windows 2016
The following list of supported the Consul releases:
- Consul 1.5+
There are some variables in defaults/main.yml which can (Or needs to) be overridden:
consul_datacenter: Controls the datacenter in which the agent is running.consul_domain: Controls the domain in which the agent is running.consul_node_role: Defines node roles.consul_version: Specify the Consul version.consul_hashiui_is_install: A boolean value, whether install the Consul hashi-ui.consul_hashiui_version: Specify the Consul hashi-ui version.consul_path: Specify the Consul data folder.consul_join_servers: Address list of servers to join upon starting up.consul_join_wan_servers: WAN Address list of servers to join upon starting up.
consul_port_arg: Defines communication port.
consul_arg.dns_allow_stale: Enables a stale query for DNS information.consul_arg.dns_max_stale: Limit how stale results are allowed to be.consul_arg.enable_local_script_checks: Enable them when they are defined in the local configuration filesconsul_arg.enable_script_checks: Controls whether health checks that execute scripts are enabled on this agent.consul_arg.enable_syslog: Enables logging to syslog.consul_arg.encrypt: Create by consul keygen, Specifies the secret key to use for encryption of Consul network traffic.consul_arg.encrypt_verify_incoming: Enables enforcing encryption for incoming gossip.consul_arg.encrypt_verify_outgoing: Enables enforcing encryption for outgoing gossip.consul_arg.https: Enables The HTTPS API.consul_arg.log_level: The level of logging to show after the Consul agent has started.consul_arg.raft_protocol: Controls the internal version of the Raft consensus protocol used for server communications.consul_arg.ulimit_nofile: The number of files launched by systemd.consul_arg.ulimit_nproc: The number of processes launched by systemd.consul_arg.use_cache: A boolean value, Whether use agent caching for http endpoints.consul_arg.verify_incoming: Enables enforce the use of TLS or verify a client's authenticity for server RPC and HTTPS API.consul_arg.verify_incoming_https: Enables enforce the use of TLS or verify a client's authenticity for HTTPS API.consul_arg.verify_outgoing: Enables enforce make use of TLS for outgoing connections.consul_arg.verify_server_hostname: Enables enforce verify the hostname of the certificate.
consul_backupset_arg.keep: The number of backups days to keep.consul_backupset_arg.cloud_rsync: Whether rsync for cloud storage.consul_backupset_arg.cloud_drive: Specify the cloud storage providers.consul_backupset_arg.cloud_bwlimit: Controls the bandwidth limit.consul_backupset_arg.cloud_event: Define transfer events.consul_backupset_arg.cloud_config: Specify the cloud storage configuration.
consul_acl_arg.enabled: Enables ACLs.consul_acl_arg.datacenter: Designates the datacenter which is authoritative for ACL information.consul_acl_arg.default_policy: The policy controls when cannot be read from the primary_datacenter or leader node.consul_acl_arg.down_policy: The default policy controls the behavior of a token when there is no matching rule.consul_acl_arg.master_token: Only used for servers.consul_acl_arg.ttl: Control Time-To-Live caching of ACL policies.
consul_dns_recursors: Specifies the address of an upstream DNS server.consul_dns_service_ttl: A TTL on service lookups with a per-service policy.
consul_performance.leave_drain_time: A duration that a server will dwell during a graceful leave in order to allow requests.consul_performance.raft_multiplier: An integer multiplier used by servers to scale key Raft timing parameters.consul_performance.rpc_hold_timeout: A duration that a server will retry internal RPC requests during leader elections.
environments: Define the service environment.datacenter: Define the DataCenter.domain: Define the Domain.customer: Define the customer name.tags: Define the service custom label.exporter_is_install: Whether to install prometheus exporter.consul_public_register: Whether register a exporter service with public consul client.consul_public_exporter_token: Public Consul client ACL token.consul_public_http_prot: The consul Hypertext Transfer Protocol.consul_public_clients: List of public consul clients.consul_public_http_port: The consul HTTP API port.
There are some variables in vars/main.yml:
- Ansible versions >= 2.8
- Python >= 2.7.5
See tests/inventory for an example.
[Master]
node01 ansible_host='192.168.1.10'
node02 ansible_host='192.168.1.11'
node03 ansible_host='192.168.1.12'
[Master:vars]
consul_node_role='server'
Including an example of how to use your role (for instance, with variables passed in as parameters) is always nice for users too:
- hosts: all
roles:
- role: ansible-role-OS-consul
consul_node_role: 'server'You can also use the group_vars or the host_vars files for setting the variables needed for this role. File you should change: group_vars/all or host_vars/group_name.
consul_datacenter: 'dc01'
consul_domain: 'local'
consul_node_role: 'client'
consul_version: '1.9.9'
consul_hashiui_is_install: false
consul_hashiui_version: '1.3.8'
consul_path: '/data'
consul_join_servers:
- '1.1.1.1'
- '1.1.1.2'
- '1.1.1.3'
consul_port_arg:
dns: '53'
dns_interface: '8600'
exporter: '9107'
hashiui: '3001'
http: '8500'
serf_lan: '8301'
serf_wan: '8302'
server: '8300'
consul_arg:
dns_allow_stale: true
dns_max_stale: '10s'
enable_local_script_checks: true
enable_script_checks: true
enable_syslog: true
encrypt: 'Ek3ceyPsJuHiWpvn/TNcUeDXiXttyMag8QTJ0qOEQOM='
encrypt_verify_incoming: true
encrypt_verify_outgoing: true
https: true
log_level: 'WARN'
raft_protocol: '3'
ulimit_nofile: '20480'
ulimit_nproc: '20480'
use_cache: true
verify_incoming: false
verify_incoming_https: false
verify_outgoing: false
verify_server_hostname: false
consul_backupset_arg:
keep: '30'
cloud_rsync: true
cloud_drive: 'azureblob'
cloud_bwlimit: '10M'
cloud_event: 'sync'
cloud_config:
account: 'blobuser'
key: 'base64encodedkey=='
endpoint: 'blob.core.chinacloudapi.cn'
consul_acl_arg:
enabled: true
datacenter: '{{ consul_datacenter }}'
default_policy: 'deny'
down_policy: 'extend-cache'
master_token: '7471828c-d50a-4b25-b6a5-d80f02a03bae'
ttl: '30s'
consul_dns_recursors:
- '223.5.5.5'
- '119.29.29.29'
- '8.8.8.8'
consul_dns_service_ttl:
'*': 60s
web: 30s
app: 30s
dbs: 5s
consul_performance:
leave_drain_time: 5s
raft_multiplier: 3
rpc_hold_timeout: 7s
environments: 'prd'
datacenter: 'dc01'
domain: 'local'
customer: 'demo'
tags:
subscription: 'default'
owner: 'nobody'
department: 'Infrastructure'
organization: 'The Company'
region: 'China'
exporter_is_install: false
consul_public_register: false
consul_public_exporter_token: '00000000-0000-0000-0000-000000000000'
consul_public_http_prot: 'https'
consul_public_http_port: '8500'
consul_public_clients:
- '127.0.0.1'Please send your suggestions to make this role better.
Please donate to the following monero address.
46CHVMbb6wQV2PJYEbahb353SYGqXhcdFQVEWdCnHb6JaR5125h3kNQ6bcqLye5G7UF7qz6xL9qHLDSAY3baagfmLZABz75