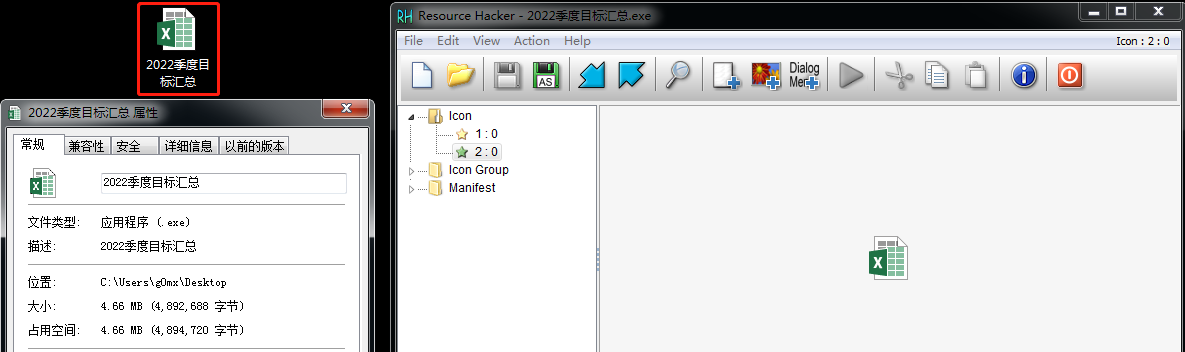
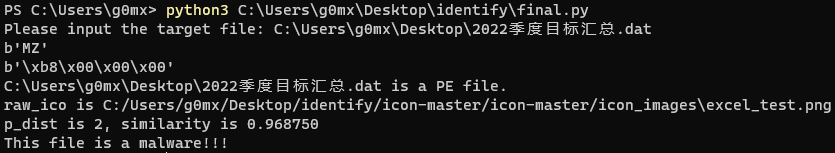
The code in this repository which function is to detect the malware that looks like a document through the icon element.
With the continuous development of network security, it is difficult for some simple attack methods to break through the defense line. Therefore, attackers often combine these simple attack methods with social engineering, and induce victims to download and execute the malicious files provided by them, so that the attack can be carried out. Among them, the most common method is to use the feature of Windows system to hide known suffixes, by replacing the icon of the executable file, modifying the name of the executable file, and disguising the executable file as a word document, excel sheet, pdf file, etc. All kinds of text files, combined with the carefully constructed phishing email, reduce the victim's vigilance of the attack and achieve the purpose of executing the malicious file. This project will detect the malware mentioned above through the icon element. And if you want know more details of this project, you can read this article I wrote.
- Language:python
- Requirements:pywin32、opencv、pillow、numpy
- System:Windows 10
- The data set of icons:
- Extract from known malicious samples
- Select from jskim90/icon
You only need to clone this repository.
After you clone this project, you only need to use "pip" install the packages.
pip install -r requirements.txt
python3 $(The path of detect_malware_by_icon.py) -h
python3 $(The path of detect_malware_by_icon.py) -f $(The path of target_file or target_dir) -P $(The path of icon database) -p $(The path of result dir)The test sample is in the folder named malware_sample. You must know this is a real malware, so please open and test it in a safe environment, such as using a virtual machine. The password of this zip is infected.
The all options of this script:
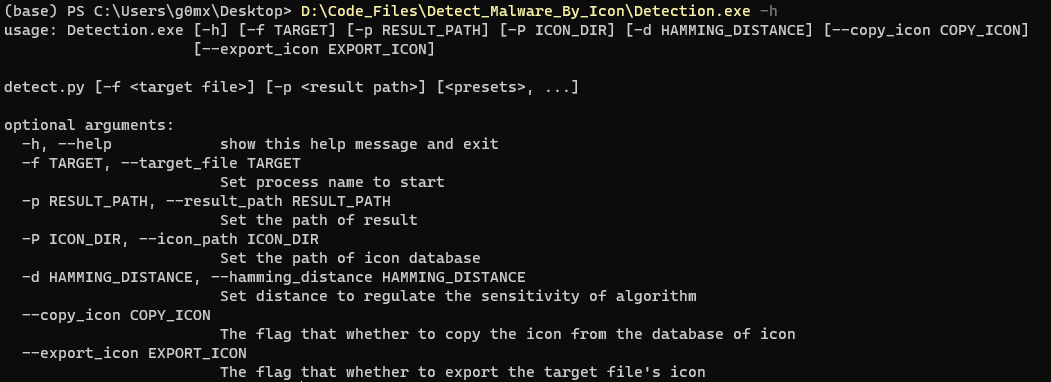
The example of this script: