The Simple SSH Honeypot Server is a script for cybersecurity enthusiasts and professionals to analyze SSH-based network interactions. Utilizing Python and the Twisted framework, this script simulates an SSH server, logging unauthorized access attempts and credentials. This is a valuable resource for understanding SSH vulnerabilities and intrusion techniques.
- Low-Interaction Honeypot: Simulates an SSH server for safely logging authentication attempts.
- Customizable Configuration: Host and port settings can be adjusted through command-line arguments.
- Detailed Logging: Records all SSH interactions, including usernames and passwords.
- Real-Time Monitoring: Enables immediate logging and reporting of SSH activities for swift detection of anomalies.
- Educational Tool: Great for learning about SSH security issues and network reconnaissance methods.
- Python 3.x
- Twisted Python library
- Cryptography Python library
To install and set up the SSH honeypot server, execute the following commands:
git clone https://github.com/0xNslabs/ssh-honeypot.git
cd ssh-honeypot
pip install twisted cryptographyStart the server with these optional parameters for the host and port. By default, it binds to all interfaces (0.0.0.0) on port 2222.
python3 ssh.py --host 0.0.0.0 --port 2222 --version "SSH-2.0-OpenSSH_7.4"All SSH interactions are logged in ssh_honeypot.log, providing detailed records of login attempts and commands issued to the server.
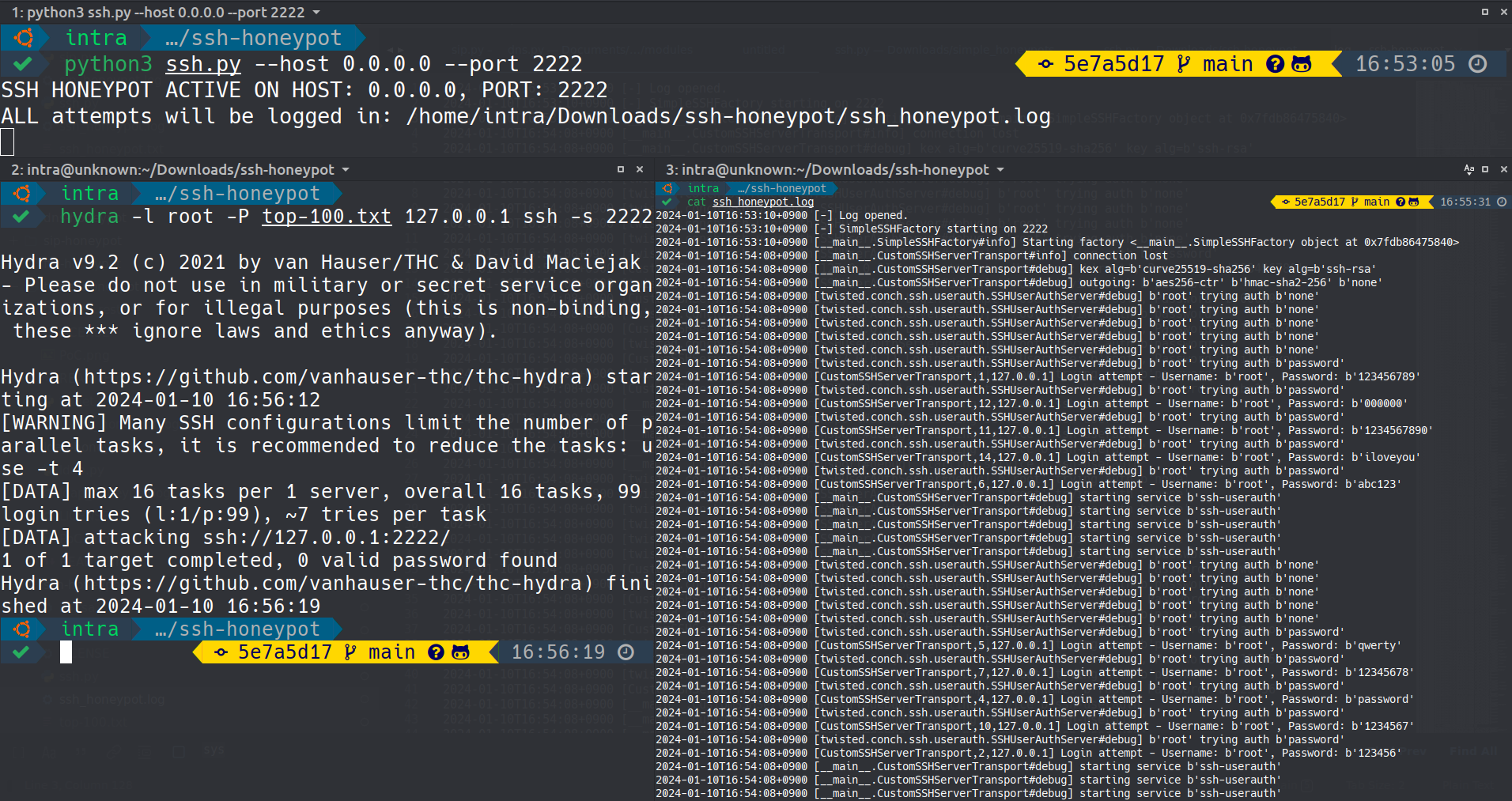 This image displays the Simple SSH Honeypot Server capturing real-time SSH login attempts and commands.
This image displays the Simple SSH Honeypot Server capturing real-time SSH login attempts and commands.
Check out the other honeypot services for monitoring various network protocols:
- DNS Honeypot - Monitors DNS interactions.
- FTP Honeypot - Simulates an FTP server.
- LDAP Honeypot - Mimics an LDAP server.
- HTTP Honeypot - Monitors HTTP interactions.
- HTTPS Honeypot - Monitors HTTPS interactions.
- NTP Honeypot - Monitors Network Time Protocol interactions.
- PostgreSQL Honeypot - Simulates a PostgreSQL database server.
- SIP Honeypot - Monitors SIP (Session Initiation Protocol) interactions.
- SSH Honeypot - Emulates an SSH server.
- TELNET Honeypot - Simulates a TELNET server.
- Caution: Employ this honeypot in secure and controlled environments for research and educational purposes.
- Compliance: Ensure all deployments comply with local and international legal standards.
This project is released under the MIT License. For more details, see the LICENSE file.