New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
28.0.3.2 → 29.0.0.19: issues about .htaccess and .well-known #2214
Comments
|
For the well known part, there are older issues where the issue has been solved by adding corresponding blocks in the nginx config. Although, the code hasn't made its way into the nextcloud repo yet: |
|
First, I used nginx as reverse proxy manager, where I had added : location /.well-known/caldav {
return 301 $scheme://$host/remote.php/dav;
}
location /.well-known/webfinger {
return 301 $scheme://$host/index.php/.well-known/webfinger;
}Second, my nginx configuration of nextcloud-fpm (raw in https://github.com/nextcloud/docker/tree/master/.examples/docker-compose/with-nginx-proxy/mariadb/fpm) had been added: location ^~ /.well-known {
location = /.well-known/carddav { return 301 /remote.php/dav/; }
location = /.well-known/caldav { return 301 /remote.php/dav/; }
location = /.well-known/webfinger { return 301 /index.php/.well-known/webfinger;}
location = /.well-known/nodeinfo { return 301 /index.php/.well-known/nodeinfo;}
location /.well-known/acme-challenge { try_files $uri $uri/ =404; }
location /.well-known/pki-validation { try_files $uri $uri/ =404; }
# Let Nextcloud's API for `/.well-known` URIs handle all other
# requests by passing them to the front-end controller.
return 301 /index.php$request_uri;
}These settings work well in 28.0.3.2, where the By the way, the |
|
Does the DNS for "yournextcloud.com" resolve to the same IP address from within the Nextcloud app container as it does from the outside? The various setup checks have been migrating from being browser based to being server-side. They run through your Either way, these sound like either upstream ( |
|
The related contents in the 'trusted_domains' =>
array (
0 => '192.168.1.100',
1 => 'yournextcloud.com',
),
'overwritehost' => 'yournextcloud.com:2443',
'overwriteprotocol' => 'https',
'overwrite.cli.url' => 'http://yournextcloud.com:2443',These settings work well in the past versions of Nextcloud. I checked the logs after I peformed a new security & setup warnings checking: According to the picture, the For some reasons, I cannot use 80 and 443 in my server, that's why I use the other port (2443) to replace 443. I don't known why the Any suggestions? |
|
I have the same problem here, I deployed it directly on the physical machine. |
|
Same issue after installation on VPS with VM script. Your data directory and files are probably accessible from the internet. The .htaccess file is not working. Has the identical setup on another VM with Nextcloud 28 no issues. |
As I said: the checks used to all (mostly) run from your browser. They are now (mostly) migrated to a new API that runs them from the server/container. This isn't a Docker matter, but a Nextcloud Server matter. It's an incremental change in progress throughout the v28+ branches. I do note your config looks odd: These contradict each other. One is using http on 2443 and the other https. Since you're using the Docker image you may also want to confirm the output of
@tinysun & @AGagarin: Then you're in the wrong place. This repository is solely for the Docker image. As it stands this Issue appears to be for matters that are a mixture of (possibly) upstream bugs (Nextcloud Server not the Docker image) or, in most cases, config matters that are arising as new problems... due to changes with how the setup checks function as of Nextcloud Server v28/v29. I suggest following up at the Help Forum. |
|
I use the nextcloud-fpm docker image with podman and nginx as proxy, and I get the same message about .htaccess which seems weird to me. Don't have the .well-known problem though, that still seems to work. |
I use different docker image and the issue is there as well from the day of update to NC29 so I'd say upstream, but more importantly; is it then: Not trying to assign blame, just gauge the extent of the issue. I'm leaning towards a) as I didn't do any config changes for months (last change was to move the whole nc dir to new mount path of a new storage) and run my nc in cloud with fair amount of firewall probing going on and the server comes up A++ in the Qualys SSL test and all the firewall probers like nikto etc. I tried got blocked before they even started by crowdsec. How could I try to access a file directly to see if it is indeed accessible without logging in to confirm whether this is indeed an issue and not just spurious warning? |
|
@hugalafutro My guess it is a false positive since that check (the data directory security check) just got migrated to a new API, but it may not be a bug necessarily (though that's certainly possible). What it does it send an HTTP/HTTPS request to all of all your I say it could be a bug, but may not be one because it may be something weird like one of your configured Related: nextcloud/server#45087 |
|
@huangwb8 Since your are getting both the data directory and the
|
Actually I just did that as well (deleted all trusted domains except for the one I am normally using) and it seems to have fixed the warning. Maybe I broke something (that list grew a bit over the years) but then I hopefully remember what I did. So thank you for giving me the push of doing this. |
|
Can confirm after removing all In In any case many thanks for pointing the right direction, although I believed there is no issue the existence of the warning kept nagging at the back of my head. |
|
Can confirm after removing all trusted_domains apart from the single domain that I have HA Proxy resolving to nextcloud, and restarting the jail, the warning is finely gone. I removed localhost and the jails local IP address. |
|
As you suggested, By the way, the Thanks for all you guys! This issue can be just closed for a while. |
|
Couldn't figure this out, then I found this and changed in previous working docker compose file. Maybe can help someone !!?? |
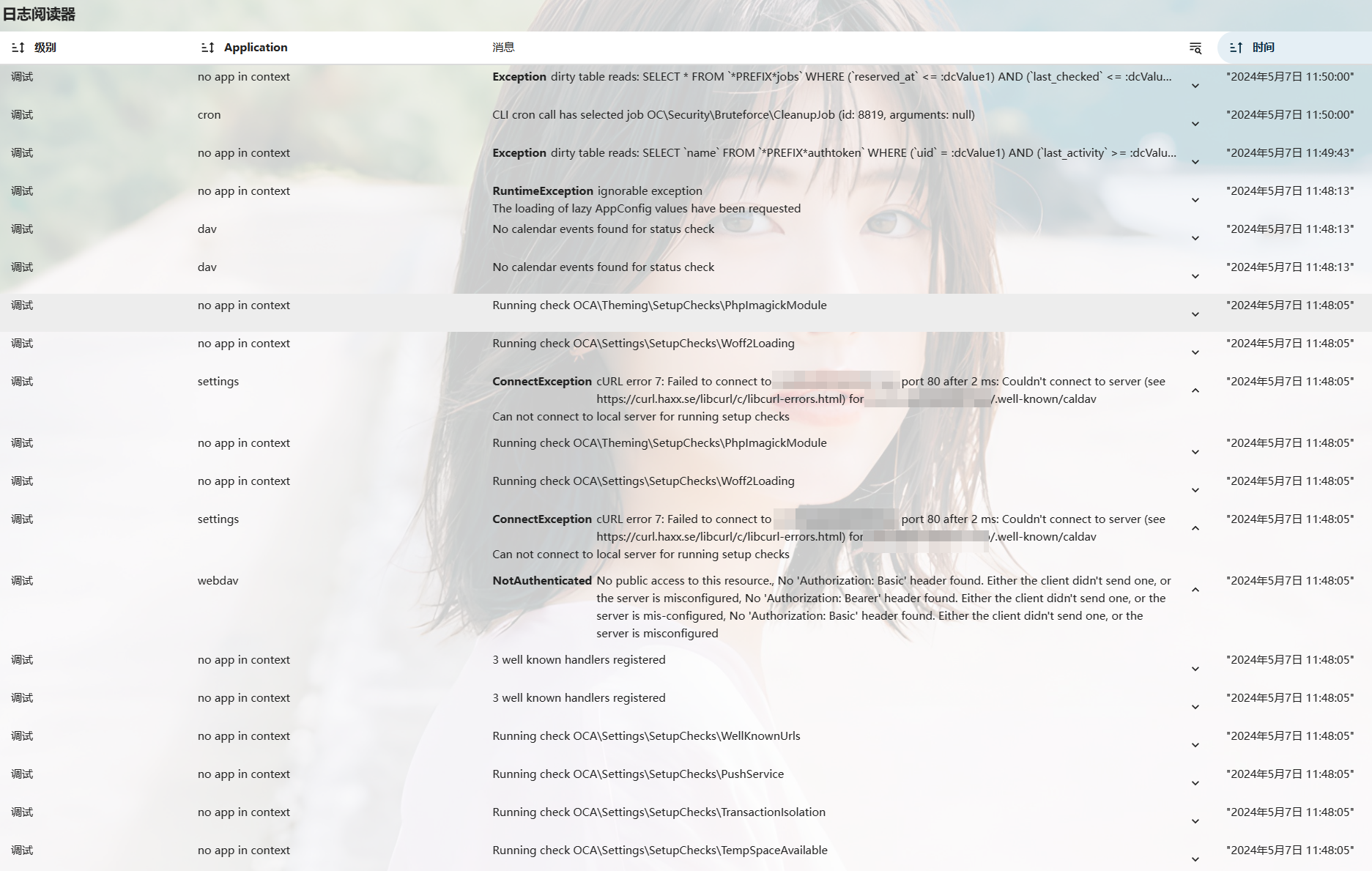
After update 28.0.3.2 to 29.0.0.19, there're 2 security & setup warnings appearing:
and
These warnings have never been shown in 28.0.3.2 or older version.
My nextcloud is built based on https://github.com/nextcloud/docker/tree/master/.examples/docker-compose/insecure/mariadb/fpm.
My update methods:
docker-compose downto set nextcloud downdocker-compose up -dto update the nextcloud imageHere is the log:
Any suggestions?
The text was updated successfully, but these errors were encountered: