veinmind-tools is self-developed by chaitin technology , cloudwalker team incubation,a container security toolset based on veinmind-sdk
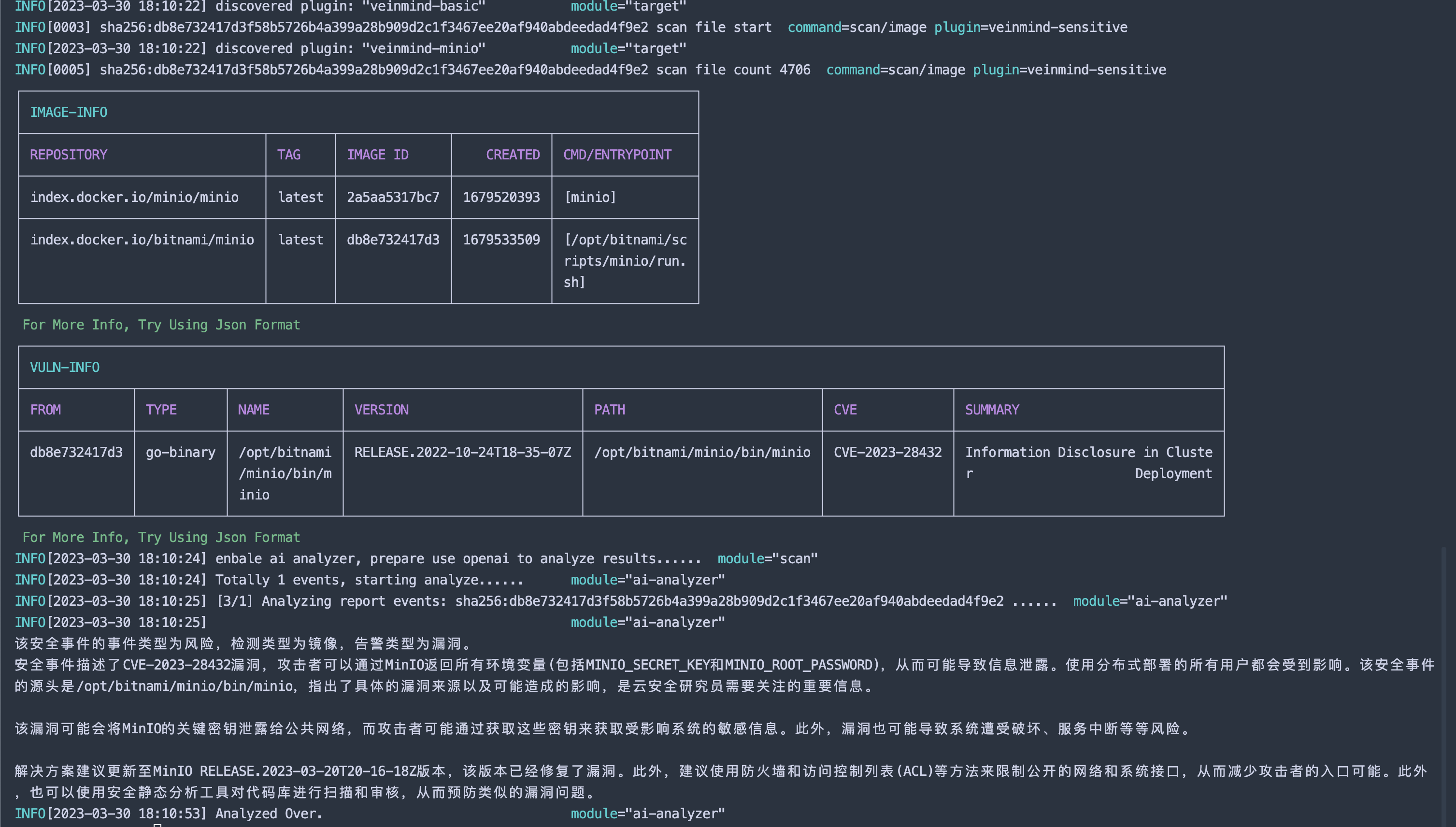
Veinmind has been connected to openai. You can use openai to conduct a user-friendly analysis of the scan results, allowing you to have a clearer understanding of the risks identified during this scan.
docker info
2. Install veinmind-runner image
docker pull registry.veinmind.tech/veinmind/veinmind-runner:latest
3. Download veinmind-runner parallel container startup script
wget -q https://download.veinmind.tech/scripts/veinmind-runner-parallel-container-run.sh -O run.sh && chmod +x run.sh
./run.sh scan [image/container]
./run.sh scan [image/container] --enable-analyze --openai-token <your_openai_token>
Note: When using openAI, please ensure that the current network can access openAI When starting a parallel container, you need to manually use docker run -e http_proxy=xxxx -e https_proxy=xxxx Set proxy (in non global proxy scenarios)
./run.sh scan [image/container] --format=html,cli
this will generate a file at path which name
report.htmlorreport.jsonyou can use,to generate different reports,like--format=html,cli,jsonwill output bothreport.htmlandreport.jsonand cli table。
| Tool | Description |
|---|---|
| veinmind-runner | scanner host |
| veinmind-malicious | Scan containers/images for malicious files |
| veinmind-weakpass | scan containers/images for weak passwords |
| veinmind-log4j2 | scan containers/images for log4j2(CVE-2021-44228) |
| veinmind-minio | scan containers/images for minio(CVE-2023-28432) |
| veinmind-sensitive | scan images for sensitive information |
| veinmind-backdoor | scan images for backdoors |
| veinmind-history | scan images for abnormal history commands |
| veinmind-vuln | scan containers/images for asset information and vulns |
| veinmind-webshell | scan containers/images for webshell |
| veinmind-unsafe-mount | scan containers for unsafe mount |
| veinmind-iac | scan images/cluster IaC file |
| veinmind-escape | scan containers/images for escape risk |
| veinmind-privilege-escalation | scan containers/images for privilege escalation risk |
| veinmind-trace | scan containers attack trace |
PS: All tools currently support running in parallel containers
Use example to create a veinmind-tool plugin quickly, see more at veinmind-example
| Name | Type | Compatibility |
|---|---|---|
| Jenkins | CI/CD | ✔️ |
| Gitlab CI | CI/CD | ✔️ |
| Github Action | CI/CD | ✔️ |
| DockerHub | Registry | ✔️ |
| Docker Registry | Registry | ✔️ |
| Harbor | Registry | ✔️ |
| Docker | Runtime | ✔️ |
| Containerd | Runtime | ✔️ |
| kubernetes | Cluster | ✔️ |
- You can make bug feedback and feature suggestions directly through GitHub Issues.
- By scanning the QR code below (use wechat), you can join the discussion group of veinmind users for detailed discussions by adding the veinmind assistant.
veinmind-tools has already joined CTStack community
veinmind-tools now joined 404 starlink project (https://github.com/knownsec/404StarLink)